Pwn2Own Ireland Day One - The Results
October 22, 2024 | Dustin ChildsWelcome to the first day of Pwn2Own Ireland 2024! We have four tremendous days of research planned, including multiple SOHO attempts. We’ll be updating this blog in real time as results become available. We have a full schedule of attempts today, so stay tuned! All times are Irish Standard Time (GMT +1:00).
That's a wrap on Day 1 of #Pwn2Own Ireland! We awarded $516,250* for 52 unique 0-days. Viettel Cyber Security (@vcslab) has an early lead for Master of Pwn with 13 points, but there's a lot of contest left to go. Stay tuned for all of the latest results as Pwn2Own Ireland continues.
*The total increased from $486,250 to $516,250 after a recount.
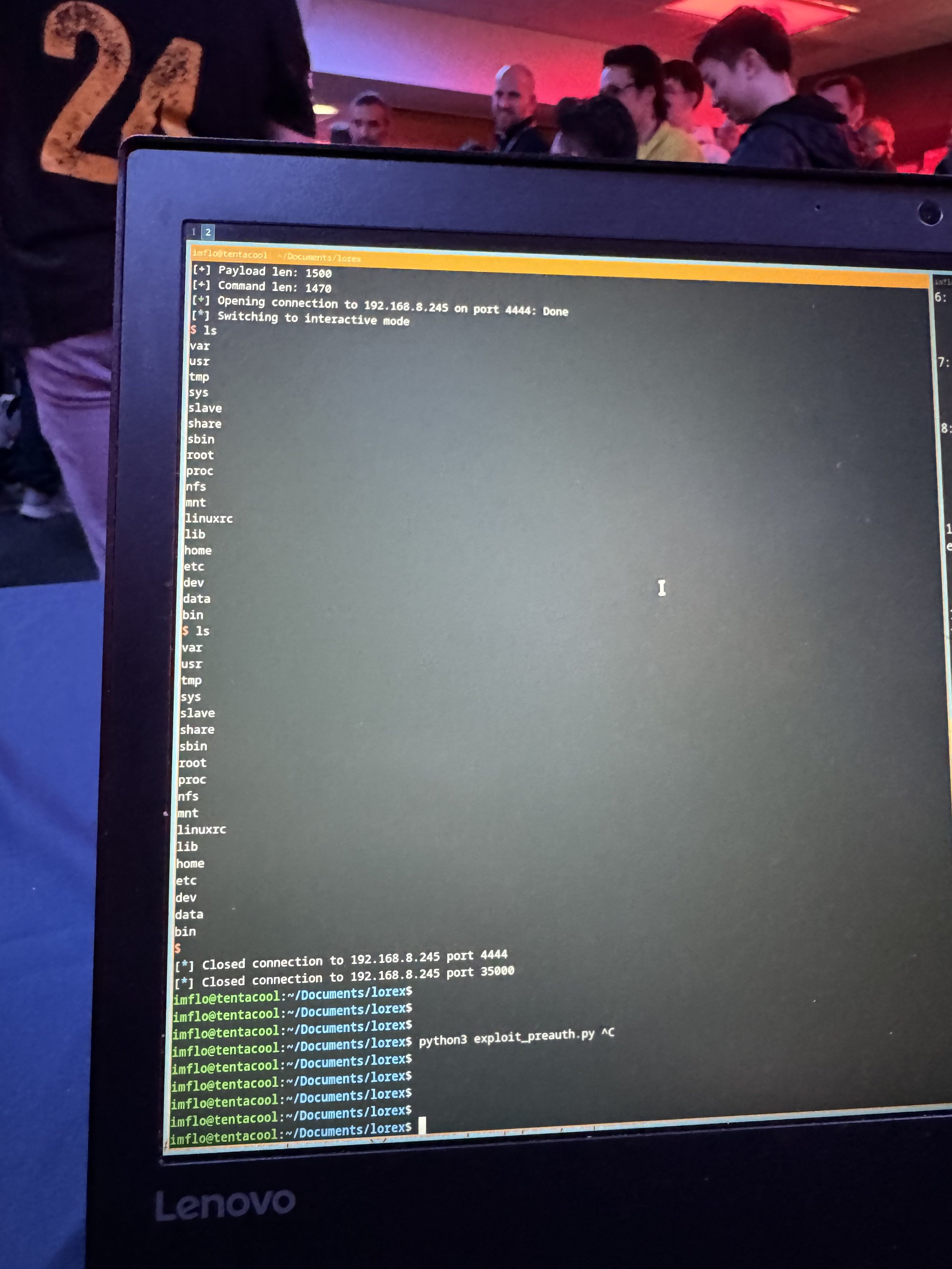
SUCCESS - phudq and namnp from Viettel Cyber Security (@vcslab) used a stack-based buffer overflow and an untrusted pointer deref to exploit the Lorex 2K WiFi camera. They earn $30,000 and 3 Master of Pwn points.
FAILURE - Unfortunately, Can Acar (@canacar_t) was unable to get his exploit of the Synology TC500 camera working within the time allotted.
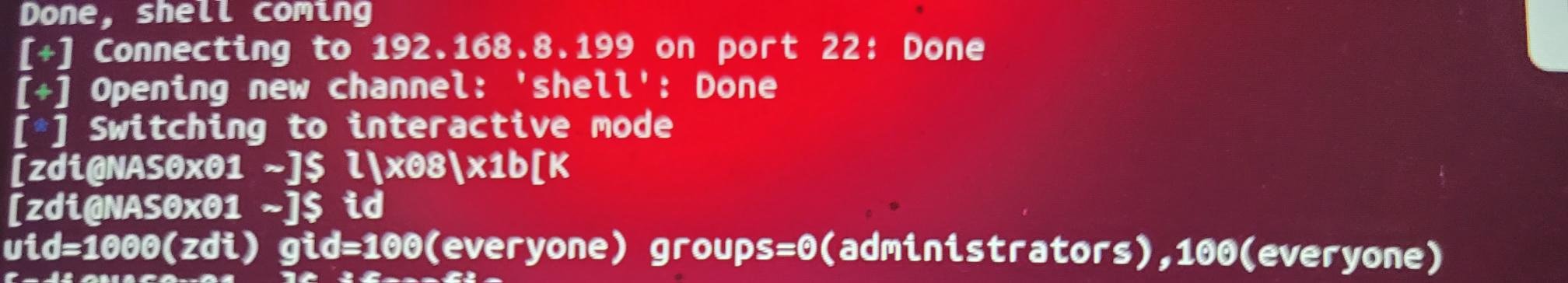
SUCCESS - Sina Kheirkhah (@SinSinology) of Summoning Team (@SummoningTeam) used a total of 9(!) different bugs to go from the QNAP QHora-322 through to the TrueNAS Mini X. His effort earns him $100,000 and 10 Master of Pwn points.
SUCCESS - Jack Dates of RET2 Systems (@ret2systems) used a single Out-of-Bounds (OOB) write to exploit the Sonos Era 300 speaker. He earns himself $60,000 and 6 Master of Pwn points.
SUCCESS - Team Neodyme (@Neodyme ) used a stack-based buffer overflow to exploit the HP Color LaserJet Pro MFP 3301fdw printer. The earn $20,000 and 2 Master of Pwn points.
FAILURE - Unfortunately, Sina Kheirkhah (@SinSinology) of Summoning Team (@SummoningTeam) could not get his exploit of the QNAP TS-464 working within the time allotted.
SUCCESS - PHP Hooligans / Midnight Blue (@midnightbluelab) used a single bug to exploit the Canon imageCLASS MF656Cdw printer. They earn themselves $20,000 and 2 Master of Pwn points.
COLLISION - The @Synacktiv team exploited the Lorex camera with two bugs, but one had previously been used in the contest. They still earn $11,250 and 2.25 Master of Pwn points.
FAILURE - Unfortunately, Sina Kheirkhah (@SinSinology) of Summoning Team (@SummoningTeam) could not get his exploit of the Synology BeeStation BST150-4T working within the time allotted.
SUCCESS - The Viettel Cyber Security (@vcslab) team combined 4 bugs - 2 in the router & 2 in the NAS - to going from the QNAP QHora-322 to the TrueNAS Mini X. Their combination of SQL injections and missing auth/exposed function bugs earn them $50K and 10 Master of Pwn points.
SUCCESS - ExLuck (@pivik_) used four bugs, including an improper cert verification and a hardcoded cryptographic key, to exploit the QNAP TS-464 NAS device. They earn $40,000 and 4 Master of Pwn points.
FAILURE - Unfortunately, Sina Kheirkhah (@SinSinology) of Summoning Team (@SummoningTeam) could not get his exploit of the Synology DiskStation DS1823xs+ working within the time allotted.
FAILURE - Unfortunately, PHP Hooligans / Midnight Blue (@midnightbluelab) could not get their exploit of the Lorex 2K Indoor Wi-Fi camera working within the time allotted.
SUCCESS - @dungnm, @dungdm, & @tunglth of Viettel Cyber Security (@vcslab) used a heap-based buffer overflow to exploit the Synology TC500. In doing so, they earn $30,000 and 3 Master of Pwn points.
WITHDRAWN - The PHP Hooligans / Midnight Blue (@midnightbluelab) have withdrawn their attempt targeting the Synology TC500 camera in the Surveillance category
FAILURE - Unfortunately, Sina Kheirkhah (@SinSinology) of Summoning Team (@SummoningTeam) could not get his exploit of the Lorex 2K Indoor Wi-Fi working within the time allotted.
FAILURE - Unfortunately, YingMuo (@YingMuo) of the DEVCORE Internship Program could not get his exploit of the Canon imageCLASS MF656Cdw working within the time allotted.
SUCCESS - The STEALIEN Inc. team [Bongeun Koo(@kiddo_pwn), Dohyun Kim(@d0now), Junyoung Choi(@insp3ct0r_x), Wonbeen Im(@D0b6y), Juhyeop Lee(@leeju_04), Juyeong Lee(@ju_cheda), GuckHyeon Jin(@nang__lam), Jongmin Kim(@slyfizz3)] used a combination of bugs in their attack chain to exploit the Ubiquity AI Bullet and flash the lights (plus get a root shell). Their work earns them $30,000 and 3 Master of Pwn points.
SUCCESS - Most impressive! Ryan Emmons (@the_emmons) and Stephen Fewer (@stephenfewer) of Rapid7 used an Improper Neutralization of Argument Delimiters bug to exploit the Synology DiskStation DS1823xs+ -- and it works or other Synology devices too! They earn $40,000 and 4 Master of Pwn points.
Failure - Unfortunately, the InfoSect (@infosectcbr) team could not get their exploit of the Synology TC500 camera working within the allotted time.
SUCCESS - The Synacktiv Team (@Synacktiv) used a combination of 3 different bug to exploit the Ubiquiti AI Bullet. All bugs were unique, so their second round win nets them $15,000 and 3 Master of Pwn points.
SUCCESS - Jack Dates of RET2 Systems (@ret2systems) used an OOB Write to get a shell and a modified login page on the Synology DiskStation DS1823xs+. His second round win nets him $20,000 and 4 Master of Pwn points.
SUCCESS - Josh Foote (@BoredPentester) used a stack-based buffer overflow to exploit the Lorex 2K Wi-Fi camera. His second round win nets him $15,000 and 3 Master of Pwn points.